Random String Alphabetic and Alphanumeric PHP Malware are a shellcode or malicious script with 8 characters random alphabetic name used for executing malicious activity and a shellcode or malicious script with 8 characters random alphanumeric name used for executing malicious activity and uploading other malicious script. At least, this is the definition based on the observation on the real incident. Before we delve deeply about this malicious script, I will discuss about the history how I know this kind of malicious script.
What is PHP Shell Backdoor ?
PHP Shell Backdoor is a malicious script with the purpose of executing malicious activity. There is multiple type of malicious activity that can be executed, which are:
-
Sending Spam
-
Gaining Privileges
-
Injecting sitemap
-
Bypassing Malware Detection for Injecting other Malicious Script (ex: fake plugin)
Those are some example of malicious activity that can be executed by PHP Shell Backdoor. Maybe there is other type of activity, but it is outside of this post scope. Now we will delve on the main topic about Random String Alphabetic and Alphanumeric PHP Shellcode or Malware.
Random String Alphabetic and Alphanumeric PHP Malware
Random String Alphabetic and Alphanumeric PHP Malware are a shellcode or malicious script with 8 characters random alphabetic name used for executing malicious activity and a shellcode or malicious script with 8 characters random alphanumeric name used for executing malicious activity and uploading other malicious script. At least, this is the definition based on the observation on the real incident. Before we delve deeply about this malicious script, I will discuss about the history how I know this kind of malicious script.
History
Before I found about the malware, I need to know some anomaly behaviour first. There is some type of anomaly behaviour, which are:
-
High Outgoing or Ingoing Traffic
-
Too Many Suspicious Identical Process Executed
-
Abnormally Slow Site and Keep Having an Error without Any Change from Authorized User
In this incident, the anomaly found is the third. After I received a report about abnormally slow site and site keeps having an error without any change, i tried to check the site directory then I decided to investigate deeply the site.
Investigation and Action
After found the anomaly, I need to check the malicious file found by malware scanner. Because i didn't find any malware from the result of malware scanning, i need to use WP-CLI to check some fake plugins with wp plugin list --fields=name,status | grep must-use | grep -v name | tail, then i found some fake plugins.

I found that there is hundreds of this fake plugins:
[wp plugin list --fields=name,status | grep must-use | grep -v name | wc -l
797But this kind of file is regarded as fake plugin because it is uploaded inside wp-content/plugins and this kind of file is also found inside other directories.
But i found that all of the file have 0 bytes size, it is indicated that the files have been deleted by malware scanner in the past but the history has been deleted so we didn't find anything in malware scanner history before.
So why did the site keep having a problem?
Because there is other malicious script undetected by malware scanner or false negative. So there is a need to find other malicious file.
Then, what do I need to do after this?
Because all 8 characters random alphabetic name malicious files are too many, it can distract me in finding the other malicious file, i need to delete all the files.
Before i deleted all the files with combination of find, grep and xargs, i need to make sure that there is no important files will be deleted by executed the command without xargs rm -f:
find . -type f -name "*.php" -size 0 | grep -P "/[a-z]{8}\.php$"Because there is some file with sub-character autoload in their name and some uppercase name file then i need to exclude them.
find . -type f -name "*.php" -size 0 | grep -P "/[a-z]{8}\.php$" | grep -v "autoload\|[A-Z]" After I didn't find any important files, then i added xargs rm -f to delete the file:
find . -type f -name "*.php" -size 0 | grep -P "/[a-z]{8}\.php$" | grep -v "autoload\|[A-Z]" | xargs rm -fThen how can find the other malicious file?
We need to check the other possible suspicious file name by using find.
find . -type f -name "*.php" | grep -P "/[a-z]{8}\.php$" 
The content of the file:

Based on our checking the file is obsfucated PHP File.
But why isn't there a PHP Start Tags
<?php?Because this is the type of malicous file that splitted in multiple files then merged together when executed to bypass malware scanner.
So we need to find the other random alphanumeric malicious files by using this command:
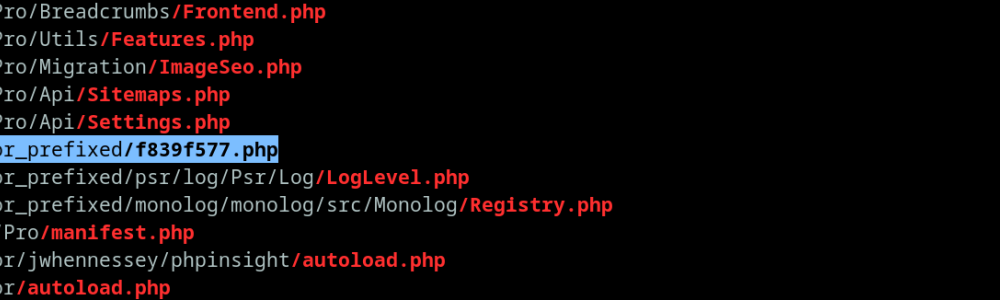
find . -type f -name "*.php" -size +0c | grep -E "/[[:alnum:]]{8}\.php$" | grep -P "\d{3}" | grep -v '[A-Z]' This command will find all PHP files with a size greater than 0 bytes, having alphanumeric names with three digits in their name and no uppercase letters.
The result:
./wp-content/plugins/wordfence/views/user/b192a6e5.php
./wp-content/plugins/really-simple-ssl/assets/css/admin/modules/1249a744.php
./wp-content/plugins/elementor/app/modules/34a49857.php
./wp-content/plugins/elementor/app/modules/kit-library/data/c294f288.php
./wp-content/plugins/elementor/core/editor/loader/4d071de5.php
./wp-content/plugins/elementor/core/editor/loader/v2/templates/ef3451dc.php
./wp-content/plugins/elementor/core/admin/0d31753f.php
./wp-content/plugins/elementor/modules/compatibility-tag/views/d747df26.php
./wp-content/plugins/elementor/assets/js/packages/editor-app-bar-ui/028514e5.php
./wp-content/plugins/elementor/assets/lib/nouislider/213e41a6.php
./wp-content/plugins/all-in-one-seo-pack-pro/vendor_prefixed/f839f577.php
./wp-content/uploads/2022/05/59b8e49d.php
./wp-content/uploads/2022/a7e18bd8.php
./backup/wp-content/plugins/updraftplus/central/css/1e006c30.php
./backup/wp-content/plugins/updraftplus/vendor/guzzlehttp/guzzle/src/e6c6a807.php
./backup/wp-content/plugins/updraftplus/vendor/composer/08419aed.php
./backup/wp-content/plugins/updraftplus/vendor/psr/http-message/src/116d66fd.php
./backup/wp-content/plugins/duplicate-page/languages/acba0821.php
./backup/wp-content/plugins/wordpress-seo/src/deprecated/frontend/eacf664c.php
./backup/wp-content/plugins/wordpress-seo/css/b330476a.php
./backup/wp-content/plugins/coming-soon/978d5448.php
./backup/wp-content/plugins/elementor/includes/template-library/sources/4e9af080.php
./backup/wp-content/plugins/elementor/includes/template-library/sources/540402e4.php
./backup/wp-content/plugins/elementor/core/settings/page/d4b26439.php
./backup/wp-content/plugins/elementor/core/files/file-types/e1821ec8.php
./backup/wp-content/plugins/elementor/modules/favorites/86238801.php
./backup/wp-content/plugins/elementor/assets/lib/eicons/a42ef416.php
./backup/wp-content/plugins/elementor/assets/lib/jquery-numerator/850eec6b.php
./backup/wp-content/plugins/elementor/assets/lib/nprogress/43e27109.php
./backup/wp-includes/php-compat/3d40059b.php
./backup/wp-includes/blocks/gallery/bcc1480d.php
./backup/wp-includes/blocks/comments-pagination-previous/6250d2d2.php
./backup/wp-includes/blocks/post-template/3147a30a.php
./backup/wp-includes/blocks/comments-pagination-next/64d5634d.php
./backup/wp-includes/certificates/8551c185.php
./backup/wp-admin/maint/e0b7558e.php
./backup/wp-admin/css/colors/light/7588670a.php
./wp-includes/js/tinymce/plugins/directionality/14189525.php
./wp-includes/blocks/paragraph/8e38986e.php
./wp-includes/blocks/page-list/7418b7a2.phpThen what do I need to do?
Because i am using malware scanner vendor who has false negative submission feature, i need to submit all this files as false negative so it is regarded as malicious in the next time scanning activity.
After I submit all the files as false negative, then i deleted all the file using:
find . -type f -name "*.php" -size +0c | grep -E "/[[:alnum:]]{2,20}\.php$" | grep -P "\d{3}" | grep -v '[A-Z]'| grep -v "wf503.php\|404.php\|503.php\|403.php\|ristretto255" | xargs rm -fYou can change the argument of grep -v with some of the files that need to be excluded.
After deleting the files, I suggest checking all vulnerabilities in the WordPress Core, WordPress Plugins, and WordPress Themes using the WP-CLI Vulnerability Scanner, then updating them. I won't discuss how to scan for vulnerabilities using the WP-CLI Vulnerability Scanner in this post because it's beyond the scope.